NFC is becoming the de facto standard for contact-less systems. For the convenience, we are potentially giving up some privacy and security.
Contactless payment technologies such as Mastercard Paypass and Visa Paywave are designed for maximum flexibility for merchants, not maximum security for customers. Some merchants may choose to have transactions processed immediately, while others may choose to process them in batch after hours. Whatever the reasons, the designers of the protocol have chosen to make the following information readable in plaintext through NFC.
- Card Number (First four digits indicate the type of card)
- Expiry
- Date and amounts of the last 10 transactions
With this information, credit card fraud can be commited. You may think that without a full name and CVV (the security number also know as the CVC or CVV2) you cannot process a transaction, however, the only number required to process a transaction is the card number. Merchants are able to pay higher processing fees to allow transactions without extra information such as the expiry and CVV. Amazon is a famous merchant that allows transactions without the security code.
Granted, you are covered if money is stolen from your account, however you need to actively check your transactions regularly for fraudulent transactions to report. This can be time consuming and difficult if you have to verify each and every transaction.
Sydney public transport users using the Opal card can provide the following information through NFC:
- Card number
- Card Balance
- Last tap details
- Transport type
- Tap on/off
- Time and Date
- Number of journeys used in the last week the card was last used
- If Auto Top-Up is enabled
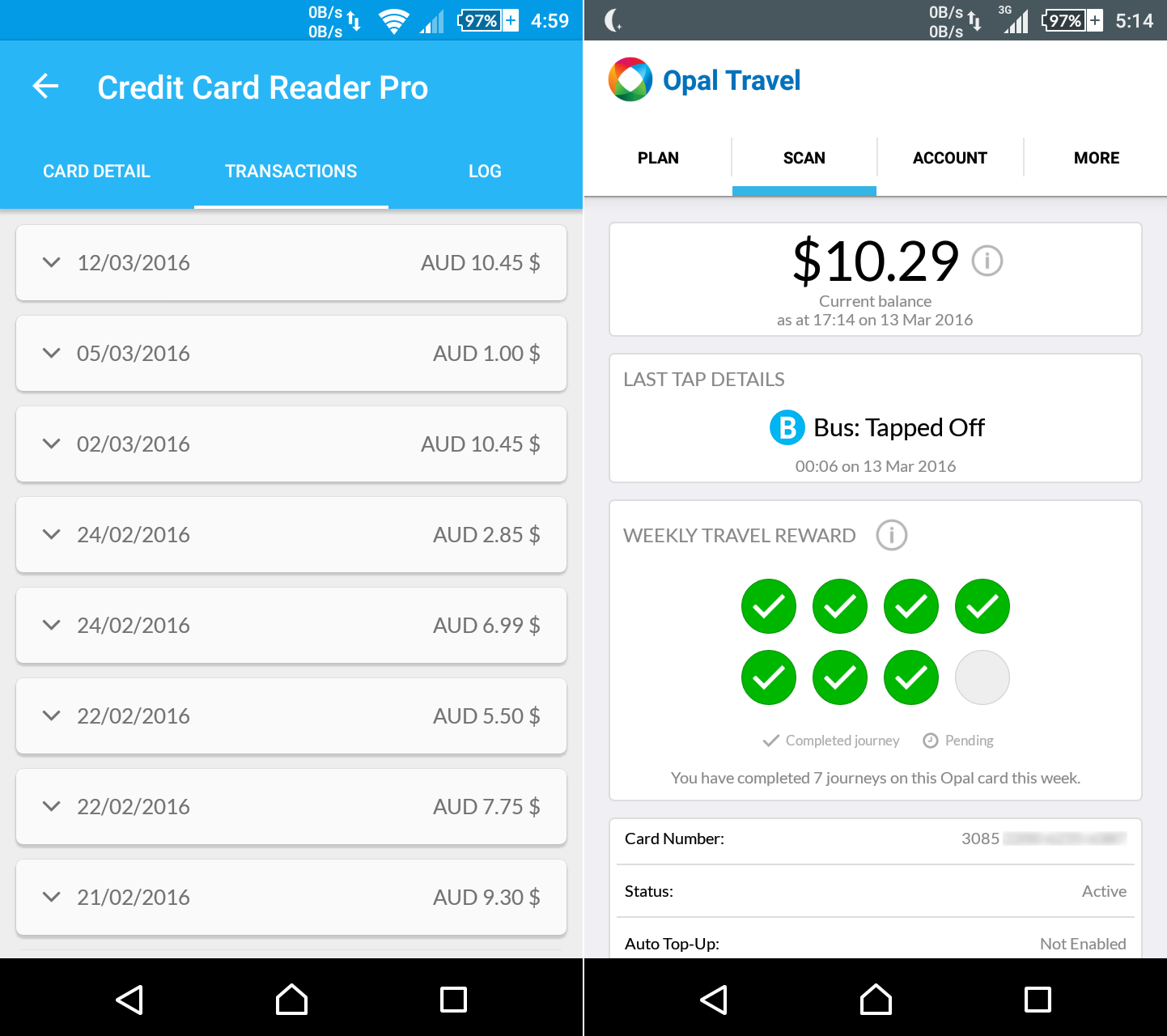
The information mentioned can be viewed easily with the Credit Card Reader and Opal Travel apps. To obtain the information, any NFC reader can be used.
To protect myself, I have been using an Eagle Creek RFID International wallet for the last two years. These types of RFID shielding contraptions are usually lined with a layer of foil to shield the magnetic fields emitted by NFC/RFID readers.
NFC/RFID communications work by the reader sending out a magnetic field and inducing it into the NFC/RFID card, which gets power through inductive coupling. The card then provides feedback to the magnetic pulses by loading down its antenna coil. The NFC/RFID reader is able to detect the card loading down the coils, and thus can read information back from the card.
The issue with passive shielding is that given a powerful enough magnetic field, you can still induce power though the shielding material. I recently got access to a more powerful RFID reader and was able to read a card though the RFID shielding wallet.
Just last week, I stumbled upon the Armourcard active jammer. The Armourcard is a jamming device as opposed to the more common shielding material. This means that there is circuitry inside the card which detects RFID/NFC signals emitted by a reader and emits its own scrambled signal to interfere with communications.

The Armourcard is credit card sized and is constructed from a double layer PCB with black solder mask. It is approximately 0.8mm thick (as thick as a credit card) around the edges and approximately 3mm thick at the bulge (the white parts of the card). The front side contains two LEDs and exposed traces that act as a touch sensitive button.
The back side holds the traces which act as the antenna coil.
The red LED flashes when the card is actively jamming a signal. The button on the front size is used to disable the jamming temporarily and to test the battery. The green LED will flash while the button is touched. As it has active circuitry inside, the Armourcard has a limited lifetime which is claimed to be approximately two years.
With the low powered NFC reader in my Xperia Z1c, the jamming LED starts flashing when the phones is 6cm away from the Armourcard. In comparison, the phone is only able to read a card when it is 3cm away from the phone. This instils some confidence as the Armourcard will always engage before the reader is able to read a card. With the Armourcard anywhere near a card, the NFC/RFID reader will fail to detect a card present.




