Defend against BadUSB in Windows
With BadUSB source codes now in the open, you may wish to protect yourself against its exploits. If you don't yet know what BadUSB is capable of, I'd recommend you watch this video: BadUSB - Accessories that Turn Evil by Karsten Nohl + Jakob Lell.
How BadUSB Works
BadUSB works by identifying itself as an input/output device (keyboard/mouse), network adapter or display to the host computer. Once your computer sees these devices, it will automatically install drivers for these devices and enable them for use. The keyboard exploit will run commands with command prompt or Windows Power shell which allows the attacker to do pretty much anything.
How to defend against it
Because device manufacturers are lazy or are trying to save money, they usually don't add unique device identifiers to their hardware. This means it is really difficult to prevent against attacks of this kind. The best solution (for now anyway) would be to not automatically install hardware of the vulnerable kind (i.e. HIDs, Keyboards, Mice, Network Adapters, Displays). Please note that if the attacker knows the make/model of the hardware currently plugged in, they could simulate its ID.
This guide will show you how to prevent Windows from automatically installing devices of certain classes. You must manually install these items if you do plug one in.
Disabling automatic device installation
-
Open the Local Group Policy editor by running
gpedit.mscor searching for Edit Group Policy in the Windows start menu.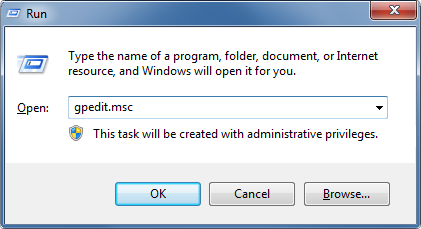
-
Navigate to Computer Configuration > Administrative Templates > System > Device Installation > Device Installation Restrictions
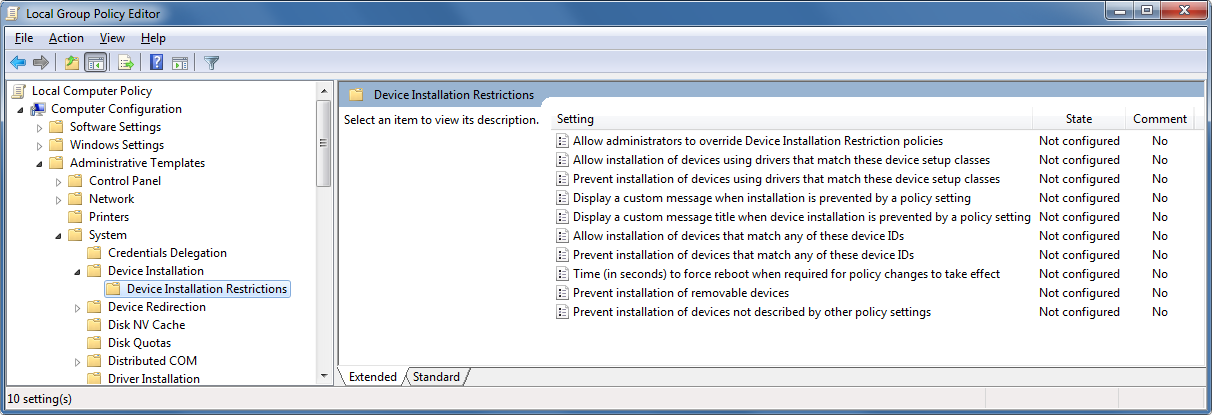
-
On the right hand side, double click on the setting Prevent installation of devices using drivers that match these device setup classes.
-
In the dialogue that pops up, select the Enabled radio option.
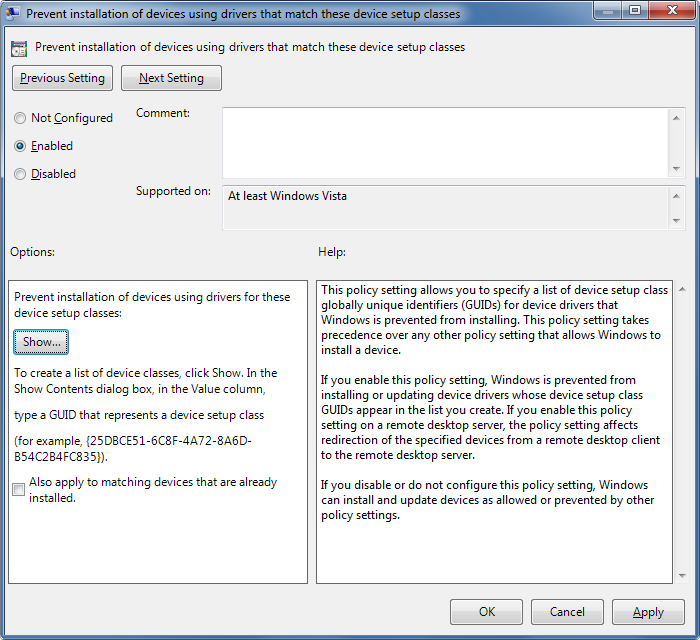
-
Then click on the Show... button under options.
-
Here, you can add the System-Defined Device Setup Classes you wish to prevent automatically installing. The devices which BadUSB exploit are keyboards, mice and network adapters. Here is a list of Class IDs which you can use. Enter one ID per cell in the dialogue.
Type Class ID Human Interface Devices (HID) {745a17a0-74d3-11d0-b6fe-00a0c90f57da}Keyboard {4d36e96b-e325-11ce-bfc1-08002be10318}Mouse {4d36e96f-e325-11ce-bfc1-08002be10318}Network Adapter (NDIS Drivers) {4d36e972-e325-11ce-bfc1-08002be10318}Network Service {4d36e974-e325-11ce-bfc1-08002be10318}Network Transport (NDIS Protocols) {4d36e975-e325-11ce-bfc1-08002be10318}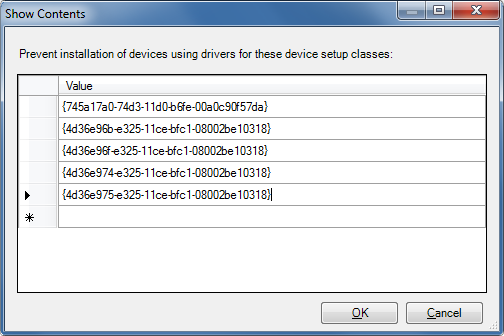
-
Click OK and then OK to save the settings.
-
If you want to have the ability to manually install the restricted devices (which is recommended), open the setting Allow administrators to override Device Installation Restriction policies and select the Enabled radio option and click OK.
Policy in Action
When a blacklisted device type is plugged into the computer, the device will not install automatically and you will be shown a tray popup.
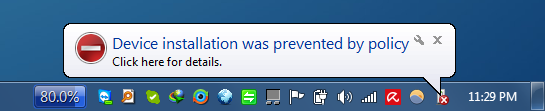
Manually installing blocked hardware
-
Open Device Manager by running
devmgmt.mscor searching for Device Manager in the Windows Start menu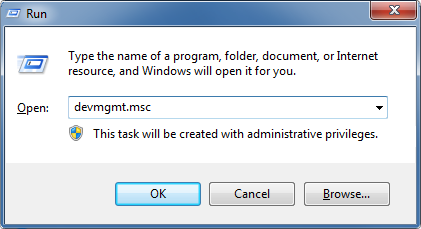
-
Devices not yet installed will show up under Other Devices. Right click on the device you want to install and select Update Driver Software
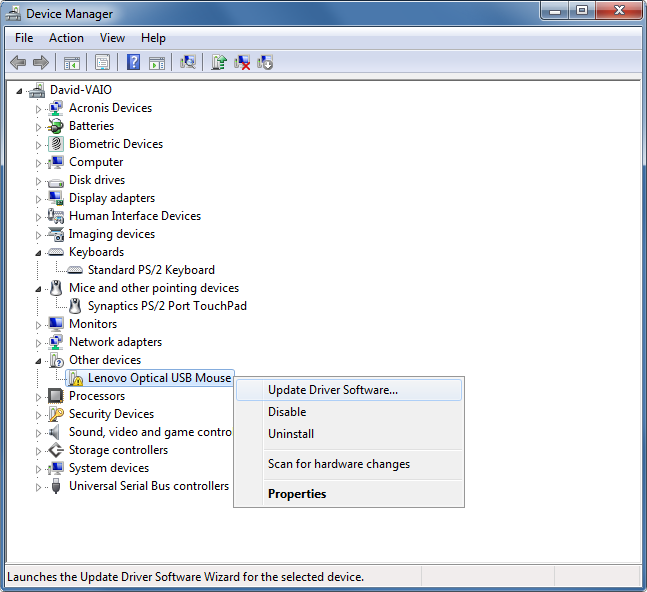
-
Then click Search automatically for updated driver software
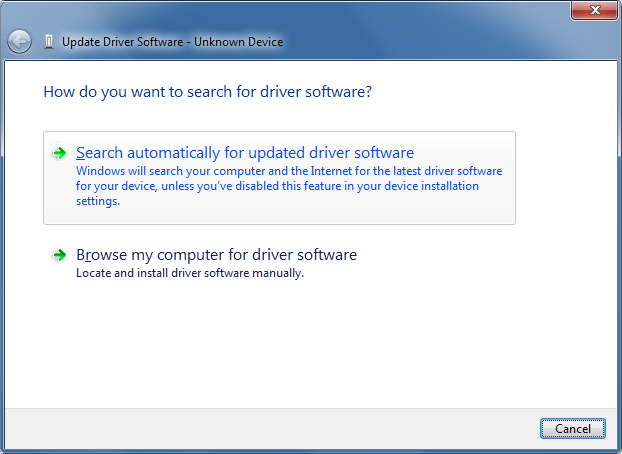
Tips for Using Windows Safely
- The best way to prevent unwanted changes to Windows system files is to use a Limited user account instead of an Administrator account. By doing this, Windows will always prompt you for the Administrator password before a program can get administrator access to your computer. This will prevent generic BadUSB attacks, as they will need your Administrator password.
- Avoid using wireless keyboards as you are broadcasting your key strokes and anyone in range can pick them up.
- If you have a wireless keyboard and mouse combo receiver and are not using the keyboard, consider uninstalling the driver for the keyboard and disabling it. This will prevent an attacker from sending keyboard input to your computer. (Windows does not allow you to disable Keyboard devices in Device Manager while they are installed. You will need to use the group policy, mentioned above, to prevent Windows automatically installing the keyboard drivers. Uninstall the keyboard and only then will you be able to disable the keyboard device.)